Cyber security is crucial for managing your data and online presence in today’s growing digital life. As we head into 2024, knowing the main types of cyber security is vital. This guide will cover the essential types of cyber security. In the upcoming year, it will assist you in safeguarding your digital assets.

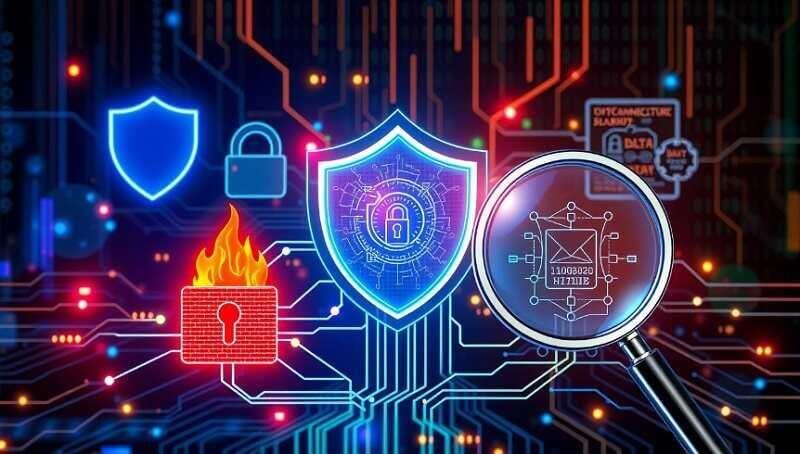
Various forms of cyber security are shown abstractly, with a network diagram showing secure connections, a firewall with digital flames, a lock signifying encryption, a shield signifying protection, and a magnifying glass analyzing data breaches, all interconnected in a high-tech environment with glowing circuits and binary code in the background.”
Key Takeaways
- Explore the evolving cyber security landscape and emerging threats in 2024
- Gain insights into the different types of cyber security measures for comprehensive protection
- Understand the differences between network, application, and cloud security tactics.
- Find out what emerging industries, like IoT and container security, have to play in the cybersecurity ecosystem.
- Find out about establishing effective security protocols and avoid being caught in a cybercriminal trap.
Understanding the Cyber Security Landscape in 2024
Cyber security and the digital world are changing quickly. You need to know about threats, digital security challenges, and the impact on businesses and people. This knowledge helps us navigate today’s cybersecurity world.
Current Cyber Threat Statistics
This makes cyber attacks increasingly common and complicated. According to the Verizon Data Breach Investigations Report 2023, phishing and ransomware assaults are on the rise.
Apart from malware and DDoS attacks, as well the threats remain big.
Evolution of Digital Security Challenges
The digital world has altered due to new technology and linked gadgets, leading to new types of cyber attacks. Cloud vulnerabilities and IoT security concerns make the digital security world complex and diverse.
Impact on Business and Individual Safety
Thus, cyber attacks can be enormous problems for businesses and people too. Data breach leads you to suffer loss of reputation and financial loss. Cyber attacks are actual, and identity theft and financial fraud are real.
| Cyber Threat | Impact on Businesses | Impact on Individuals |
| Attacks by Phishers | Financial losses, reputational harm, and the loss of private information | Financial fraud, identity theft, and compromising personal information |
| Ransomware Incidents | Disruption of operations, financial losses, data loss | Loss of personal files and documents, financial extortion |
| DDoS Attacks | Service interruption, outage, and income loss | Communication and Internet service disruption |
Businesses and individuals need to be aware of the developing cybersecurity landscape. This knowledge helps protect digital assets in the future.

A cityscape full of technological bones, glittery circuits in the sky, bright blue and green colors as data flows through, representations of firewalls and encryption, wedging technology together with nature with trees as part of the infrastructure, symbols of cyber protection and digital locks floating in the air, twilight and all.
Cybersecurity Types: A Detailed Overview
This digital world is being used today, so if you want to enjoy your online life, you need to know about cyber security. Here are a few strategies for self-defense. Let’s look at the significant types of cybersecurity that are changing digital security.
Network Security
Network security protects the digital paths we use every day. It includes firewalls, systems for detecting intrusions, and VPNs. These tools keep your network safe from cyber threats.
Application Security
With more software and web apps, application security is more important than ever. It focuses on keeping apps’ code and interfaces safe, which helps protect data from harm.
Cloud Security
Cloud computing has brought new challenges to cyber security. Cloud security protects cloud data and systems. It also manages access and keeps data safe, adapting to the cloud’s fast changes.
Emerging Technologies
New techs like IoT and AI are changing cyber security. Securing these technologies needs special knowledge and new ways to protect them.
This is a visually striking representation of various types of cybersecurity, featuring abstract icons and symbols for network security, endpoint protection, cloud security, data encryption, and threat detection. Elements like shields, locks, firewalls, and digital circuits are included in a futuristic setting with vibrant colors and dynamic shapes that convey the complexity and importance of cybersecurity in a modern digital landscape.
Knowing about the significant types of cybersecurity helps you stay safe online. It prepares you for the future of digital protection.
Network Security: Methods for Infrastructure Protection
In today’s world, it’s essential to secure your network. The most important for your data are Firewalls and systems for detecting intrusions. We’ll explore how to strengthen your network’s defenses against network security attacks.
Firewall Implementation Methods
Firewalls are your network’s first defense. They control who can access your system. It is best to use both hardware and software firewalls. Ensure you update your firewall rules often to fight new network security attacks.
Systems for detecting intrusions
Systems for detecting intrusions (IDS) work alongside firewalls. They watch for suspicious activity and alert you to types of network security attacks as they happen. Having network-based and host-based IDS gives you a complete picture of your network’s security.
VPN and Secure Communication
With more people working remotely, VPNs are crucial for safe communication. They create encrypted paths for data to travel. Ensure your VPN is strong, and teach your team how to use it to keep your network safe.
| Network Security Measure | Key Benefit | Potential Drawbacks |
| Firewalls | Blocks unauthorized access and monitors network traffic | Can be complex to configure and maintain |
| Systems for detecting intrusions | Detects and alerts on suspicious network activity | May generate false positives, requiring careful monitoring |
| Virtual Private Networks (VPNs) | offers routes of communication that are safe and encrypted. | impacts network performance and involves user training. |
Firewalls, intrusion detection systems, and VPNs help protect your digital world. Security should continually be updated. You can fight off-network security attacks and keep your data safe.

A futuristic cityscape with glowing digital networks weaving through buildings depicts a strong shield symbol integrated into urban architecture. It features high-tech surveillance systems and secure data centers illuminated by blue and green lights, surrounded by a complex web of interconnected devices and secure servers, emphasizing the theme of network security and infrastructure protection.
Application Security and Data Protection
Our digital world is changing fast, and safeguarding it has never been more critical. We need to know about application security and data protection, which are key to keeping our online lives safe.
Applying security fixes is a significant component of application security vulnerabilities. These include injection flaws and cross-site scripting (XSS) attacks. By fixing these, we ensure our apps can fight off cyber threats.
Data protection is also crucial. It keeps our sensitive information safe from bad actors. Implementing stringent access restrictions and strong passwords guarantees the security of our data.
| Types of Application Security | Types of Application Security Vulnerabilities |
| Input Validation Authentication and Authorization Session Management Cryptography Error Handling Logging and Monitoring | Injection Flaws Broken Authentication Sensitive Data Exposure Cross-Site Scripting (XSS) Security Misconfiguration Using Components with Known Vulnerabilities |
We can make our apps safe by knowing about application security and fixing vulnerabilities. This way, we keep our data and users free from cyber threats. The band is about being proactive in the fast-changing world of cybersecurity.
Cloud Security and Emerging Technologies
A quick overview of the cyber security world. With cloud computing and all sorts of new technologies like the Internet of Things, new challenges exist. Businesses need strong cloud security and ways to fight off new threats.
Cloud Infrastructure Protection
Its key to protecting data is keeping cloud infrastructure safe. More stoppers use multi-factor authentication, encryption, and access controllers to prevent unauthorized access. Regular checks for vulnerabilities and good plans for security issues are also necessary.
Container Security Measures
Containerization technology is becoming more popular, but it brings new security issues. It’s essential to ensure secure image builds and have strong access controls. Also, understanding the software supply chain is crucial. This includes scanning for vulnerabilities and using secure platforms for container orchestration.
IoT Device Security
More IoT devices linked result in a more considerable attack surface. It’s vital to protect these devices with a multi-layered approach. This includes secure onboarding, firmware updates, and data encryption. Network segmentation is also crucial to limiting damage from breaches.
| Cyber Security Domain | Key Security Measures |
| Cloud Infrastructure Protection | Multi-factor authentication Encryption Access controls Vulnerability assessments Incident response planning |
| Container Security | Secure image builds Access controls Software supply chain management Vulnerability scanning Secure container orchestration |
| IoT Device Security | Secure device onboarding Firmware updates Data encryption Network segmentation |
As cyber security keeps evolving, businesses must stay alert. They need to protect their cloud, containers, and IoT devices. Using the right security strategies, they can stay safe from new threats.
Conclusion
This guide has shown you how important cyber security is for protecting your digital stuff. It covers everything from network security to cloud protection. Cybersecurity keeps changing to fight new threats from hackers.
Using a mix of cyber security and staying up-to-date can help. It can lower the chance of data theft and other cyber attacks. Always be ready and watchful to keep your digital world safe.
As you explore the digital world, remember these cyber security tips. Be ready to change your approach as new dangers arise. Knowing about different types of cybersecurity helps protect your personal and professional life in the tech world.
FAQ
What kinds of cybersecurity are there?
Cybersecurity has several types. Among these are cloud security, application security, network security, and IoT device security. Together, they protect our digital world.
Which are the primary categories of cybersecurity?
These traditional extensive areas are network, application, and cloud security. Network security guards the infrastructure. Application security protects software and data. Cloud security tackles cloud-specific issues.
What are the types of network security?
Network security has a few main types. Firewalls and systems for detecting intrusions are critical. Also, VPNs ensure secure communication. These help keep the network safe from threats.
What are the types of application security?
Application security deals with many vulnerabilities. It includes fixing input validation flaws and access control issues. Secure coding and regular checks are vital. Application firewalls also play a significant role.
What kinds of attacks are there against network security?
Network attacks come in many forms: injection, phishing, DDoS, and man-in-the-middle attacks, which are common threats. Attacks with these attacks intend to disrupt or steal significant data.
In that case, what types of application security vulnerabilities exist?
Application vulnerabilities are a big concern. XSS, CSRF, SQL injection, and insecure references are some. These can let attackers in, steal data or run malicious code.
You can also read related articles:-